Editorial Update
This blog originally used the word whitelist to describe a list that allows an application to run. This word has been replaced with allowlist. This is both a more accurate word and more inclusive.
Introduction
First, a little background, I've spent most of my time in Windows. As a Windows admin I fell in love with AppLocker. These days I find myself spending more time with MacOS and I've been looking for a way to secure MacOS in a similar way
That brings me to Google Santa. This product has a few things that drew me to it.
- It's updated regularly, as of writing this article the most recent build is 7 days old
- It has Certificate, Path, and Hash rule capabilities, similar to AppLocker.
- Simple setup and configuration.
This blog will bring you through initial setup of Google Santa and the linked GitHub repo contains a selection of SHA256 certificates needed to allowlist specific applications
Setup
Setup for Santa is extremely straight forward.
- Install Precompiled Signed Binary
- Set Santa to enforce
vi /var/db/santa/config.plist
- Change key
clientmodeinteger to2
- Change key
By default Santa allowlists Apple certificates. This is an anti-lockout 'feature'. By putting Santa into enforce mode, everything is now blocked except Apple applications.
Important Files, Directories, & Commands
While using Santa these things will be extremely useful to understand.- Santa Configuration
less /var/db/santa/config.plist
To understand more about configurable options with Santa review Configuration - Review Logs
less /var/db/santa/santa.log
This will show you what's blocked, whats allowed, etc. The cert_sha256 hash shown in the log can be used to create allowlist rules - Find Certificate Information
santactl fileinfo /Applications/%app% - Allowlist an Application
santactl rule --whitelist --certificate --SHA256 %SHA256_of_app% - View the rules database.
/bin/launchctl unload /Library/LaunchDaemons/com.google.santad.plist
/usr/bin/sqlite3 /var/db/santa/rules.db ".dump" >> /tmp/rules_playback.sql
/tmp/rules_playback.sql
/bin/launchctl load /Library/LaunchDaemons/com.google.santad.plist
Allowlisting an Application - WebEx Network Player
In this example WebEx Network Player has already been installed prior to enabling Santa, as such, we can
try to launch it and get a failure

To enable WebEx as Root perform the following:
- Monitor Logs using
tail -f /var/db/santa/santa.log | grep --line-buffered WebEx | grep DENY - Launch WebEx Network Player
- Review logs looking for
cert_sha256= - Add to Santa SHA256 rules (as of 20170921)
santactl rule --whitelist --certificate --sha256 ed3dc18e83b80201e1f16ae27a37e3cac7636744bae5ae8286509f64f8730292
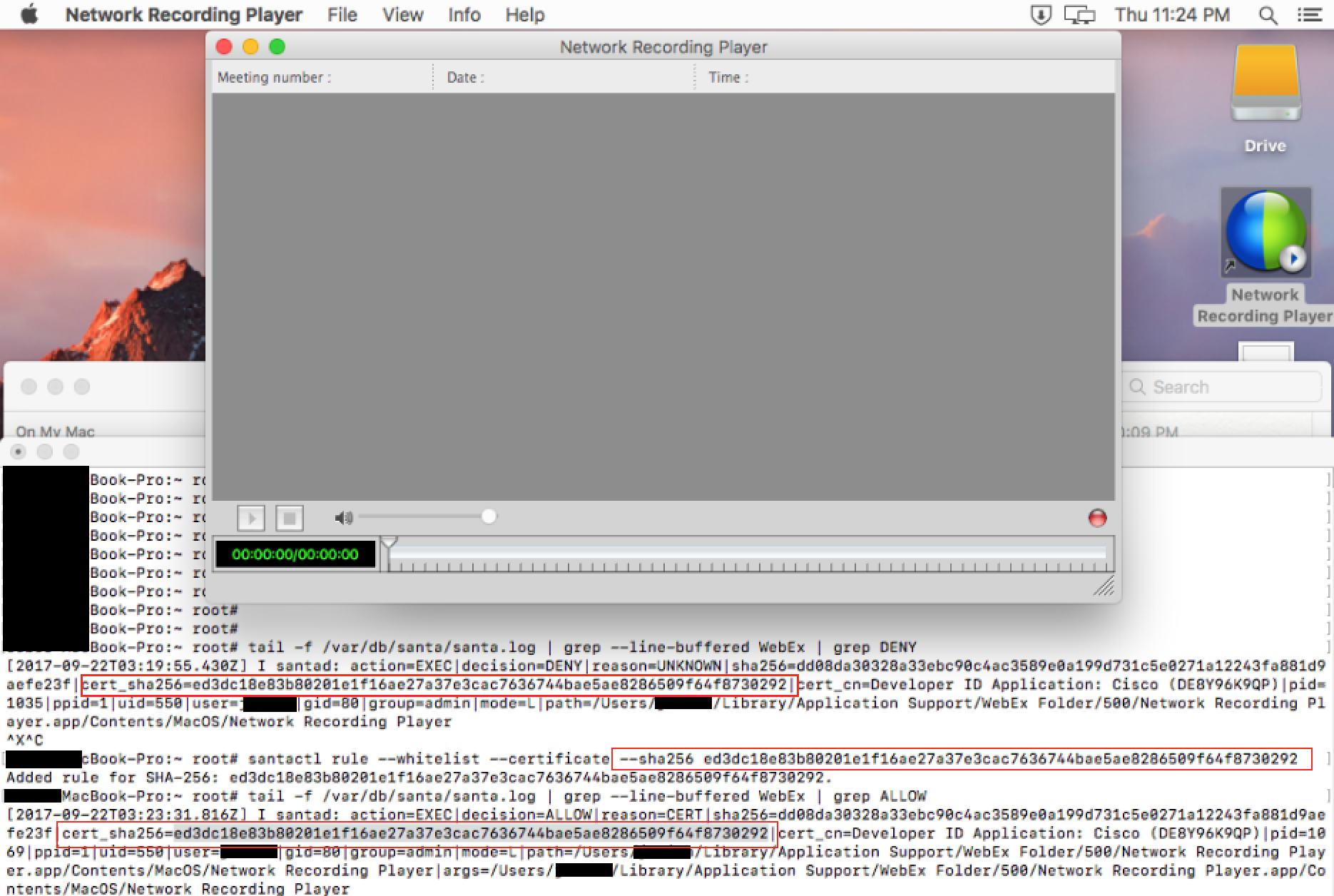
Note some applications require multiple certificates. Google Chrome's updater uses a different cert than Google Chrome itself. Be on the lookout for this behavor.
Conclusions
This should give you enough information to start allowlisting the apps on your laptop that you trust and to deny the ones you don't
To help get you started I've uploaded to github https://github.com/vgrsec/googlesantarules some scripts for some common applications.